Importance of Cyber Security Globally
Internet-based industry such as e-commerce, banking, traveling, insurance and cloud-based is giving high priority to the cyber security. However, companies also accept their safety does not reach to optimum level because they lack of proper security related education in their organization. According to ITRC (Identity Theft Resource Center) report, until July 2016, there were more than 522 data breaches. The report also states that data breach is now diversifying into different sectors such as federal agencies, healthcare, and telecom. Many popular companies such as Centene, Federal Bureau of Investigation, Seagate and Internal Revenue Service are the notable examples of data breach in the USA. Such data breaches cause loss of personal information like Name, Contact Number, Social Security Number and ID cards on a large scale. In 2016, the total cost of cybercrime reached to $450 billion globally. There are various types of cybercrime attacks used by cybercriminals for various purposes such as data breach, vulnerability and much more. The major cyber-attacks are.
- Cyber Fraud
- Malware Attacks
- Social Engineering Attacks
- Technical Attacks
- Vulnerability Exploitation
- Login Attacks
#1. Cyber Fraud Cyber fraud is a process where cybercriminal tries to steal your money, personal, property and financial information. There are different types of cyber fraud such as Phishing attacks, Spear Phishing attacks, unauthorized disclosure, and Whaling.
#2. Malware Attacks
in this type of attack, the malware comes from specific files such as .exe source and adware. The virus activates just after you open the file and in cases, malware file download on your PC without your authorized approval.
#3. Social Engineering Attacks
This attack is currently popular because it targets mainly to non-technical person through the phone internet call such as Skype. They present themselves as company authorized or technical support guys and asked for your personal information such as name number and Ids for regular database updates.
#4. Technical Attacks
Mainly target Organization technical systems such as Database, DNS, and outdated software. There are different types of Technical Attacks that hackers are using and DOS attacks are one of the well-known types, where attacker disrupts the internet usage of the user. Web Page Defacing is a type of attack where a hacker breaks the web page security and change to page visibility such as design and text to warn the owner about the lower level of data security.
#5. Vulnerability Exploitation
Make sure you get your software update from authorized source, because most of the vulnerability attacks come with software updates. In Vulnerability attacks, hackers inject the code in the program, and when the user tries to run that program, the hackers get their desired result.
#6. Login Attacks
Such attacks directly target your personal accounts such as email, bank and social media platforms. Some common login attacks are brute force, password cracking and oAuth exploits. The hackers mainly target large firms such as Google, Microsoft and Sony. Therefore, such companies have some strong organization security rules for their employees. But it doesn't mean small and medium firms are safe. Every organization must set some strict rules to avoid major security threats. Below are some common security rules that every company must follow.
- Keep your necessary software and system up to date.
- Create an internal policy to avoid using external drive such as pen drive, memory card or external hard disk with informing technical person. Also block certain website such a free software download, free shareware, and spam sites responsible cyber-attacks.
- Cloud service is adopted by many companies because cloud service is cost efficient and easy to access from anywhere.
- Educate your employee about cyber threats and how you can avoid malware downloads.
- Encourage your employee to use a secure password (alphanumeric, symbol) and change after a period.
Benefits Of Domain Validation (DV) SSL Certificates
Have you ever think, that how much your website is secure from hackers, spyware and malicious attacks? In the recent report of Kaspersky Lab states that last year 47.48% financial, 10.17% E-Shop, 25.76% E-banks and 11.55% E-payment attacks blocked by their security software. If you think your website is having spyware, then you need to think twice before login in your admin panel. If you are running a small-scale website like blogs or a medium scale website like a locally targeted online store, you must take advantage and secure your site through inexpensive Domain Validation Certificates.
Important Checklist for Website Security
Whether you are launching a new website or running a successful existing online business/personal website, you must check your system security frequently to avoid unpredictable cyber and malware attacks. Last year 51% percent of US adults suffered from some security vulnerability issue also estimated global cost of the cyber-attack reached to $400 yearly. Nowadays website security is important for everyone whether it is small blogger, locally based online store or large e-commerce seller. If your site is dealing with user data such as name, email, postal address and card details then you must check below mention tips to avoid any loss hacking and malware attack.
There are various small factors responsible for big cyber and malware attacks, which administrator does not take into account. Some common factors responsible for malware attacks are outdated CMS, old password and not using secured encryption connection.
To prevent your website vulnerabilities and compatibility issue, keep your Content Management System (CMS) up to date. World`s most popular CMS like WordPress, Joomla, and Drupal frequently update their system and send the notification to their user. Make sure you update your CMS, important plugins, and software to avoid general malware and breach issue.
Some most common login passwords like "admin" admin123" and "password" are very easy to crack. Keep your password strong and must be having alphanumeric and special character. Change your password after a certain time to avoid any misuse. Keep your security question uncommon and never disclose the answer to anyone.
Websites like blogs, News and E-commerce place some JavaScript for data validation. Sometimes these data are validated through client-side, but sometimes it is not safe because hackers can easily catch your password from the page source. Data validation from server side adds an extra layer of data security because it follows some certain safety rules to block malware software intended to breach user data.
Scheduling an automatic backup may save your time and money every time. Backup take some extra space from your current storage space. However, it's good to keep the backup on a regular basis.
When we talk about data security. SSL Certificate is the most important option available for encryption. SSL certificate like Comodo SSL, Symantec SSL, RapidSSL and Thawte SSL certificates are some of the most popular brands in Data security & encryption industry. Based on your website nature and requirement you can buy SSL certificate start from $11 with instant issuance.
SQL Injection is some of the most popular techniques used by hackers to grab personal information. Through placing a dynamic code in the query server, hackers can easily access your website personal information like user name, address and credit card details. Some common guidelines to avoid SQL injection vulnerabilities are.
With these common recommendations, you can protect your important data hacking and malware attacks. Help you to build strong customer trust and improve sales.
There are various small factors responsible for big cyber and malware attacks, which administrator does not take into account. Some common factors responsible for malware attacks are outdated CMS, old password and not using secured encryption connection.
#1. Keep Software Up to Date:
#2. Use Secure Passwords & Update frequently
#3. Data Validation Must Be Done from Server-Side
#4. Backup Regularly
#5. Set up SSL Connection
#6. Reduce SQL injection vulnerabilities
- Validate all SQL input correct
- Use predefined query instead of a dynamic query.
With these common recommendations, you can protect your important data hacking and malware attacks. Help you to build strong customer trust and improve sales.
Why Your Website Need SSL Encryption Security?
Nowadays everyone likes to purchase from the website, and online transaction is a big part of that. In a recent report, cybercrime found that more than 30,000 websites are infected every day with malware and their data stolen by unknown hackers. The primary reason for website hacking and malware attacks are using old version CMS (Content Management System) and plugin for long-time and sometimes not using SSL (Secure Sockets Layer) Certificate on the website.
Medium and Small scale business sites such as personal blogs, local stores, and local news sites are easy targets for online hackers because those website does not plan to spend on their website data security. Without encryption security, hackers can steal your private data such as email address, password, and credit card details and can easily misuse them. According to Wall Street Journal, the estimated loss from cybercrime is $100 billion every year. If you are running an online business or any online activity where customers need to share personal details, then your website needs SSL encryption protection.
SSL Certificate creates an encrypted connection between server and browser through a key pair (a public and a private key). These certificates also contain website owner information, which is known as "Subject.".
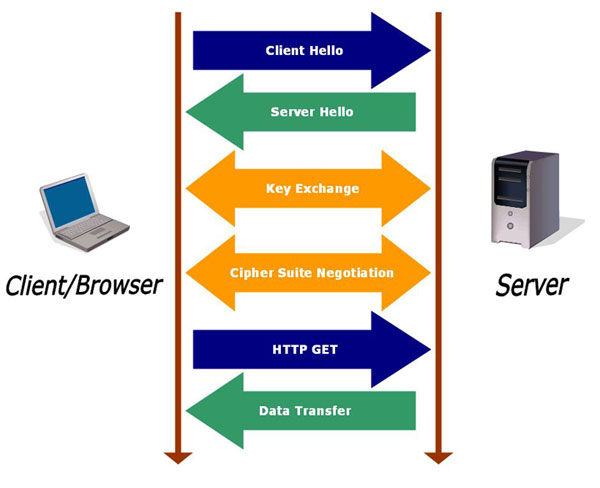 To get an SSL certificate, you need to first create a CSR (Code Signing Request) on your website hosting server. This process gives you two pair of keys (Public and Private Key) file.
Once you received the CSR data file, you need to send the public key file to SSL Certificate issuer also known as Certificate Authority or CA. When SSL Certificate issuer received the public key file, they create a structure to match your private key. The SSL Certificate issuer can never see your private key data.
After the completion of SSL certificate verification, when a browser tries to access your website protected by SSL certificate, the browser and server connect through SSL connection. Anything sends from the browser in encrypted form through public key can only decrypt from the private key install on the server.
To get an SSL certificate, you need to first create a CSR (Code Signing Request) on your website hosting server. This process gives you two pair of keys (Public and Private Key) file.
Once you received the CSR data file, you need to send the public key file to SSL Certificate issuer also known as Certificate Authority or CA. When SSL Certificate issuer received the public key file, they create a structure to match your private key. The SSL Certificate issuer can never see your private key data.
After the completion of SSL certificate verification, when a browser tries to access your website protected by SSL certificate, the browser and server connect through SSL connection. Anything sends from the browser in encrypted form through public key can only decrypt from the private key install on the server.
Any online business whether large, medium or small scale required SSL certificate to meet Card Payment Industry guidelines. PCI (Payment Card Industry) verify the SSL certificate is obtain from a trusted SSL authority and providing a secure private connection in the pages where customer needs to enter their personal details.

Replicate or fraud website do not get SSL certificate easily. If a visitor is completely aware of SSL protection, they will simply move from such untrusted website without any further action.

A Customer can easily check whether the website is secure from SSL certificate with the help of site seal and green bar. Website with SSL certificate will increase customer trust and confidence of online purchase.
What Happen When You Do Not Use Data Encryption

Medium and Small scale business sites such as personal blogs, local stores, and local news sites are easy targets for online hackers because those website does not plan to spend on their website data security. Without encryption security, hackers can steal your private data such as email address, password, and credit card details and can easily misuse them. According to Wall Street Journal, the estimated loss from cybercrime is $100 billion every year. If you are running an online business or any online activity where customers need to share personal details, then your website needs SSL encryption protection.
What is SSL Certificate
SSL Certificate creates an encrypted connection between server and browser through a key pair (a public and a private key). These certificates also contain website owner information, which is known as "Subject.".
How SSL Certificate Works

Benefits of SSL Certificate
Essential in Online Payment System:
Any online business whether large, medium or small scale required SSL certificate to meet Card Payment Industry guidelines. PCI (Payment Card Industry) verify the SSL certificate is obtain from a trusted SSL authority and providing a secure private connection in the pages where customer needs to enter their personal details.
Protection against Phishing:

Replicate or fraud website do not get SSL certificate easily. If a visitor is completely aware of SSL protection, they will simply move from such untrusted website without any further action.
Improve Customer Trust:

A Customer can easily check whether the website is secure from SSL certificate with the help of site seal and green bar. Website with SSL certificate will increase customer trust and confidence of online purchase.
Types of SSL Certificate
There are various types of SSL certificate products and brands are currently available in the market, based on your website type and requirement you can buy SSL certificate. For better understanding, you can also visit SSL Certificate Finder page.Some Popular SSL Certificate Products
- Single Domain SSL Certificate
- Multi Domain SSL Certificate
- Extended Validation (EV) Certificate
- Organization Validation SSL Certificate
- Wildcard SSL Certificate
Conclusion
A perfect SSL certificate can improve visitor trust through its green padlock, https protocol encourage visitor's to make the transaction with confidence.Cyber Security Awareness Program (CSAP) for Organizations
CSAP: An inevitable task for an every organization
How much employees in your organization are aware of cyber security. The big question is threatening every organization in this age is security of their cerebral property. On one side, cyber crime is stepping quickly in our daily life. Organization and web users are still not aware about this rising risk of the Cyber Crime. How organizations can fight against rising cyber crime? The simple answer is bringing security awareness in every department of organizations. Conduct a security awareness program for the entire organization and provide security training for selected employees according to business requirements.When employees fall into a cyber culprit?
Employees innocently access to malicious websites or download software that contains malware or virus. They click on spam emails or phishing emails, which can redirect them to a phishing site to steal their information or money. Sometime employees share their password to an unknown person or transfer data with plugging infected USB drives, which can lead them into trouble.
What should include Cyber security Awareness Program?
CSAP – Cyber Security Awareness Program is essential part of organization. Oregon Government has approved a plan in 2006 to implement security awareness training. The security awareness should obey the following IT standards, laws and regulations, and official guidance documents as:- ISO 17799
- COBIT 4.0
- HIPAA (Privacy & Security Rules)
- GLB-A
- PCI Data Security Standard
- FISMA
- NIST SP 800-16
- NIST SP 800-50
- Section 508 of the Rehabilitation Act
- Oregon Accessibility Policy
Best Practices for Security Awareness Program:
The Best Practices identified by the Oregon Government for security program are as follows:- Security awareness program is compulsory for the entire staff.
- All third parties who have access to the organization's information should participate in the security program.
- The program should start with the introduction of an organization's security policy and expectations.
- The entire staff must recognize about the organization's information security policy.
- At least once per year, the entire staff should have security training.
- Periodic reminder should be sent to all the employees.
- Management leaders must attend a security program.
- Security awareness must be given according to the base of roles and responsibility of employees.
- Common level of security training should be given to all staff.
- Security awareness program should comprise information of known threats, security needs, legal liabilities, business controls, contact person for incident reporting.
- Employees should be advised about the importance of security in their personal life.
- Take a help of external training experts and benchmark for further guidance.
- IT tools should be used to automate training session.
- Records of staff training should be kept in staff records.
- Use qualitative and quantitative metrics for getting feedback and check the effectiveness of the program.
Few DON'Ts:
- Do not ignore Training content Update:
- Do not stick with old training program and keep it updated. It should be relevant, precise, and interesting for the employees.
- Do not rely on only White paper Training:
- Make some interesting video and PowerPoint for training program purpose instead of printed white paper. Run a training video contest for the user that fills employees with excitement and energy.
- Do not puzzle between cyber security awareness and security training:
- Cyber security awareness changes the behavior of individuals that strengthens security culture while security training provides knowledge about different security aspects.
- Do not ignore anyone:
- Set a security awareness program for every employee of the organization. This is the best way to mitigate security risk in an organization.
- Do not focus only on security compliances:
- Security awareness is a continuous process therefore, cover every topic, and keep updating it according to business and technology changes.
Few DOs:
- Take Support of top Management Executives:
- Compel top executives and middle managers to attend the security awareness program to make other employees aware about their experience.
- Conduct Program in an interesting way:
- Add competition or learning techniques in security program to make the entire program effective and interactive.
- Use different sources of information:
- Always use images, newsletters, and blogs to provide refreshing security information to keep trainees updated.
- Focus on awareness material:
- Make a useful and flexible awareness material that employees can use it outside the work premise and can share with family / friends to spread security awareness.
- Get feedback and measure success:
- Get the feedback of employee's like and dislike, effectiveness of the program, and take suggestions to make a better awareness program.
Correlation between Dedicated IP and SSL
What is Dedicated IP exactly stand for? This is indeed a basic question that needs to be understood by any techno savvy person. However, before going to reveal about dedicated IP let us understand IP address. IP address serves two main functions including network interface identification and location addressing. Generally, there is 32-bit IP address is in use, which is known as IPv4 but due to growth of internet, IP designers now using 128-bit IP address, which is called IPv6.
There is a lot of debate on whether to choose dedicated IP or not, we have to look at dedicated IP, and other aspects.
Dedicated IP can also provide website speed though multiple source of traffic is handled by a single IP. Every server examines a packet, and request and then deliver the traffic to particular domain. In this case, number of destination is not significant, the process of website loading time can be slightly influenced which is not a serious concern.
What is Dedicated IP?
It is easy to remember and assigned to each device that is participating in computer network used for communication. A dedicated IP is only devoted to a single server and not shared with other server. Many shared hosting providers charge normal fee to provide dedicated IP.Speed and Dedicated IP:
Dedicated IP can also provide website speed though multiple source of traffic is handled by a single IP. Every server examines a packet, and request and then deliver the traffic to particular domain. In this case, number of destination is not significant, the process of website loading time can be slightly influenced which is not a serious concern.
Why SSL needs Dedicated IP?
When you have ecommerce website where online shoppers carry online transactions with their debit-credit card, or with online banking, you need an SSL on your website to protect ongoing transactions between the user and the company server. SSL certificate authenticates the server with IP address and verify the IP address assigned to the particular server. When a client connects to the server for a different domain name, the server gets confused about which certificate to show to the client. This process is defined in below example.Example of SSL and Static IP:
For instance, there are two domains called www.abc.com and www.xyz.com and both domains are hosted on a single IP address (for example 000.000.0.0). Now a person has opted SSL for a domain called www.abc.com on his website with that IP address. However, the person wants to access https://www.xyz.com the browser will check for SSL and if it is fail to make secure connection for particular website, then browser will show a name mismatch error.Advantages of Dedicated IP:
- You have less downtime compare to Shared IP.
- If you are ecommerce merchant then you should have your own SSL with a dedicated IP.
- Many web-hosting providers need a unique IP to access anonymous FTP function.
- Shared IP address may have security threat due to shared among multiple website while dedicated IP has less chance of security threats.
- With static IP, you will have easy remote access of your PC from wherever you operate it.
- There are chances of blacklisted website on shared IP address (If there is blacklisted website) on contrary, dedicated IP has less chance of blacklisted.
Alternate Solutions to Dedicated IP:
- SNI (Server Name Indication): SNI is an extension to SSL that allows the client to include hostname in the first SSL handshake so, the server identifies the correct virtual host name for which the request is made, and the server can easily set up the connection.
- Wildcard Certificate: Using Wildcard certificate user can secure unlimited sub domains under a single IP address. You can include sub domains like www.example.com, webmail.example.com etc.
- SAN Certificate: Subject Alternative Name (SAN) can secure up to 25 domain names, sub domains with a single certificate.
Viber came again under attack of Syrian Electronic Army
Viber’s Apple App store is again under cyber attack of Syrian Electronic Army. It is time to rethink for cyber world because hackers are in mood to debase credibility of cyber world. If we see in the past two weeks, we have seen many hackers debasing giant companies’ account and their development center like Instagram account, Apple’s Dev Center, and famous Viber app.
Viber is a cross platform VOIP (voice over internet protocol) was established for iPhone in Dec 2010. Viber features text, image, and video messaging around all platforms like iPhone, Android and Microsoft’s Windows Phone. At present Viber holds 30 languages and is now compatible with window and Apple PC.
Moreover, Viber is the latest example of such a malicious action performed by Syrian Electronic Army that attacked on Viber’s Apple App Store account by changing the description of Viber’s IOS app.
Viber authority persons gave statement in previous attack that no sensitive data was exposed and only two systems: a customer support panel and a support administration system were under attack. Below are two images of Viber spokesperson’s statement.

We are facing duos situation in this cyber world as we see technology development and on other side emerging threat of hackers. A common person who relies on technology cannot understand the technical language of hackers instead rely on companies’ products by putting complete trust. Therefore, it clearly states that it is time to wake up from dream that no one seems to be secure in this unpredictable technology world, it is an alarm for the whole cyber world as you could be the next target of these culprits.
Viber is a cross platform VOIP (voice over internet protocol) was established for iPhone in Dec 2010. Viber features text, image, and video messaging around all platforms like iPhone, Android and Microsoft’s Windows Phone. At present Viber holds 30 languages and is now compatible with window and Apple PC.
Moreover, Viber is the latest example of such a malicious action performed by Syrian Electronic Army that attacked on Viber’s Apple App Store account by changing the description of Viber’s IOS app.
"We created this app to spy on you, Please Download IT”
According to 9to5Mac report hackers have taken responsibility of this attack and tried to reach to Viber authority for further clarification. Last week we noticed the attack on Viber done by the same authority called Syrian Electronic Army. It is assumed that hackers have also access to other developing functions that is indeed a serious issue for company and its customers as well. 9to5Mac’s Mark Gurman proposes the hackers could have reached access to Viber’s iTunes Connect account by a phishing fraud.Viber authority persons gave statement in previous attack that no sensitive data was exposed and only two systems: a customer support panel and a support administration system were under attack. Below are two images of Viber spokesperson’s statement.
The two statements clearly states that the two statements are differed it seems Viber is not showing transparency to its customers. Viber was hacked on 23 July 2013 by Syrian Electronic Army intimated users to stay away from Viber. Viber has 200 million users globally.

We are facing duos situation in this cyber world as we see technology development and on other side emerging threat of hackers. A common person who relies on technology cannot understand the technical language of hackers instead rely on companies’ products by putting complete trust. Therefore, it clearly states that it is time to wake up from dream that no one seems to be secure in this unpredictable technology world, it is an alarm for the whole cyber world as you could be the next target of these culprits.
Syrian Electronic Army attacked Viber - A free calling software
Viber is a free call and messaging service used for Apple and Android Platform suffered from Syrian Electronic Army’s hacking attack, yesterday on 23 July 2013 Syrian Electronic Army hacked support page and left the page with message that is shown in the below image.
Viber is a cross platform VOIP (voice over internet protocol) was launched for iPhone in Dec 2010. Viber involves text, image, and video messaging throughout all platforms iPhone, Android and Microsoft’s Windows Phone. It currently supports 30 languages and now available on window and Apple PC. Even hackers also disclosed some phone numbers, email addresses of Viber admin department and told that they have captured and downloaded some part of data backups. Viber support page now appears like this.
Hackers also said that they still possess control over the system and have deleted the page “https://wa.viber.com/csrapp/home.html”used for account management and hosted on address. Hackers have provided a screenshot that reveals phone numbers, UDID, IP address and registration details. It is really a serious damage caused to Viber. If we see the defaced webpage, all the numbers carry dialing code 963 that is of Syria.
Viber is a cross platform VOIP (voice over internet protocol) was launched for iPhone in Dec 2010. Viber involves text, image, and video messaging throughout all platforms iPhone, Android and Microsoft’s Windows Phone. It currently supports 30 languages and now available on window and Apple PC. Even hackers also disclosed some phone numbers, email addresses of Viber admin department and told that they have captured and downloaded some part of data backups. Viber support page now appears like this.
Syrian Electronic Army was previously succeeded in stealing data of True Caller and Tango app websites and deleted an article published in Daily Dot website and warned Daily Dot that if they publish any article in future, they will delete the whole website.
Cyber attacks are evolving day by day and have not even left giant social media and search engines; it causes serious concern over user’s data. It affects the credibility of a company. Phishing, man in middle attack, certificate breach, DDoS attacks are some recent attacks that have affected cyber world and forced giant corporate and social media to think over these attacks. It is a sure question arises in our mind “Do we live in hacker’s world or else hackers live in our world”.
Some sort of cyber policies should be there to fight against such hackers otherwise; the days are not far, where people avoid dealing with internet and social media.
Subscribe to:
Comments (Atom)





















